Securing user data and controlling access to resources are more important than ever. To achieve this, technologies like OAuth and JWT play a crucial role in ensuring safe and efficient user authentication and authorization.
While both are widely used in modern web and mobile applications, they serve distinct purposes and often work together. But what exactly sets them apart?
In this article, we'll break down the key differences between OAuth and JWT, explore their roles in authentication and authorization, and help you understand when and how to use them in your applications.
What is OAuth?
OAuth is a standard protocol that allows users to give websites or applications access to their information on another service without sharing their passwords.
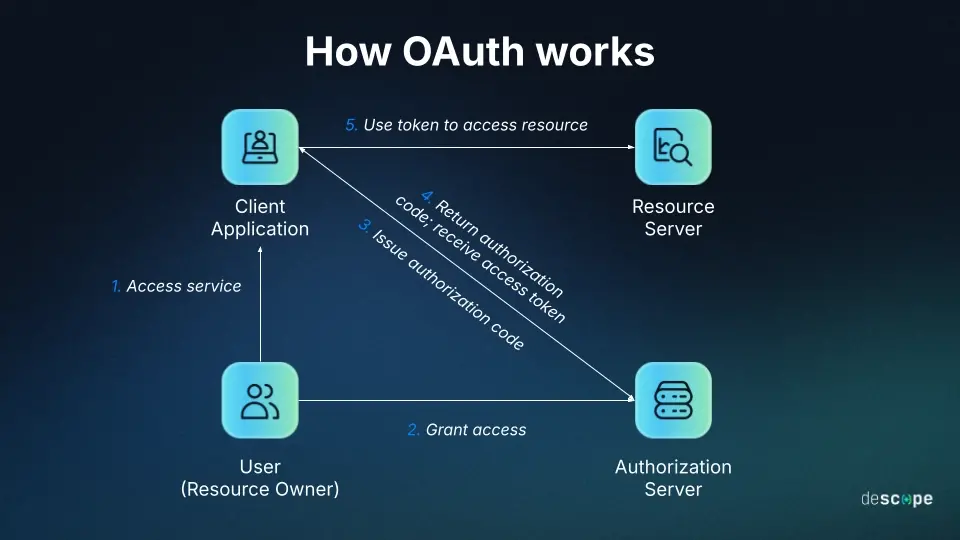
How OAuth Works
OAuth uses tokens, typically access tokens and refresh tokens, to grant permissions for actions. Here’s a simplified flow:
1. Authorization Request: The user wants to grant a third-party application (the client) access to their account (resource owner). The client redirects the user to the authorization server.
2. User Grants Access: The user logs in and is presented with a consent screen to allow the client to access specific resources.
3. Authorization Code (OAuth 2.0 Flow): If the user agrees, the authorization server redirects back to the client with an authorization code. The client then exchanges this code for an access token.
4. Access Token Usage: The client can now use the access token to request resources from the resource server on behalf of the user. The token has a set expiration time.
5. Refresh Token: If the access token expires, the client can use the refresh token (which has a longer lifespan) to request a new access token from the authorization server.
This flow ensures that the user's credentials are never exposed to the client application. Instead, the client uses limited-scope and limited-duration access tokens to perform actions.
Key points to note about OAuth
Authorization (not authentication): OAuth is primarily used for authorization, not authentication. It is about giving access to certain parts of an application or resources without exposing credentials. If you're using a service like “Log in with Google” on a third-party website, OAuth is likely at work.
Protocol-based: OAuth is a protocol, not a technology. It provides the rules and flow for secure authorization, but doesn't specify how to implement tokens or how the authorization process should look. This allows flexibility for different platforms and services.
Roles Involved in OAuth: OAuth defines a few essential roles that interact in the authorization flow:
- Resource Owner: The user who owns the data or resources being accessed.
- Client: The third-party application requesting access to the resource owner’s data (e.g., a social media app).
- Authorization Server: The server that authenticates the user and issues the access tokens to the client.
- Resource Server: The server hosting the protected resources that the client wants to access (e.g., an API that holds user data).
OAuth’s flexibility and focus on secure, delegated access make it a powerful tool for managing permissions in modern applications.
What is JWT?
JWT (JSON Web Token) is a compact, URL-safe means of representing claims to be transferred between two parties. It's a standardized token format used for securely transmitting information. Often, JWT is used alongside OAuth to encode and pass authentication data, allowing for secure communication between a client and a server.
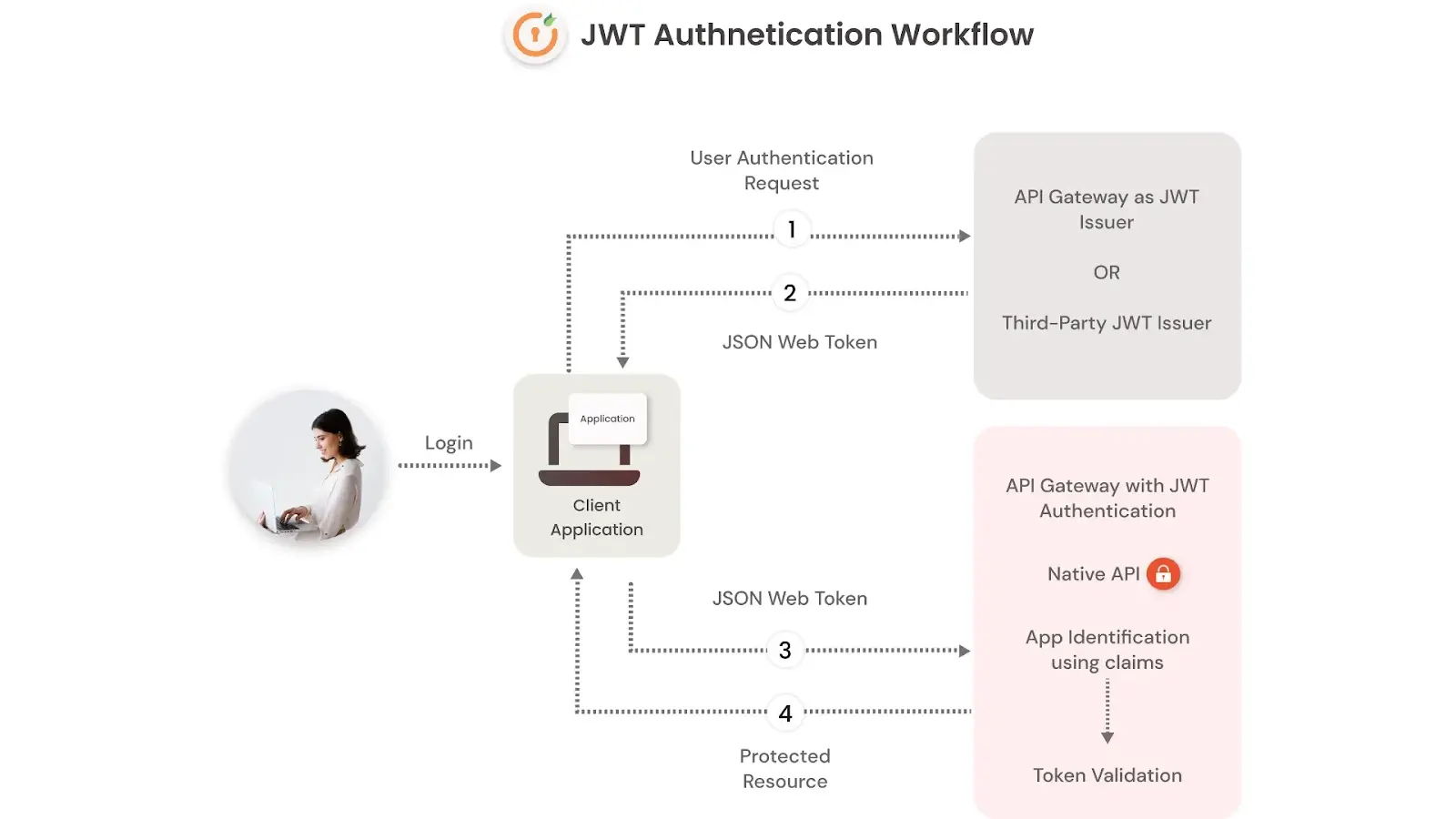
In a nutshell, JWT allows you to encode data (such as user information or permissions) in a compact format that is easy to transfer across network protocols like HTTP, without risking sensitive information exposure.
How JWT Works
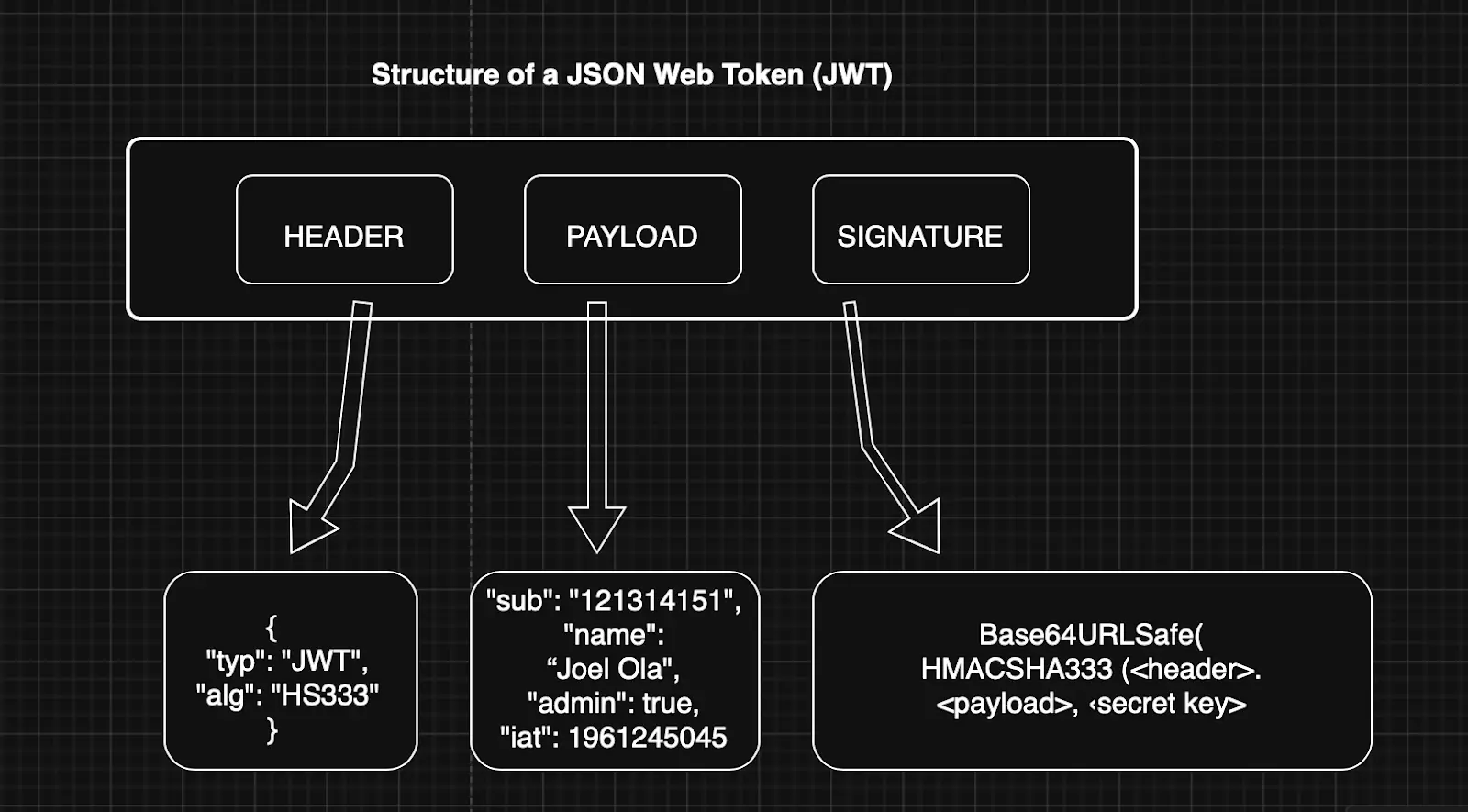
A JWT consists of three parts: header, payload, and signature. These parts are encoded using base64url, making them safe for inclusion in URLs or HTTP headers.
Header: The header typically contains the token's type (JWT) and the signing algorithm being used (e.g., HMAC SHA256 or RSA).
Payload: The payload contains the claims. Claims are information like the user’s ID, token expiration time, roles, or any other custom data. It’s important to note that the payload is not encrypted, so sensitive information should not be stored here unless it's further encrypted.
Signature: The signature ensures the token has not been tampered with. To create the signature, the header and payload are base64url encoded, then combined with a secret key (using the algorithm specified in the header). The signature is what makes the JWT secure because, if the payload or header is altered, the signature will no longer match.
When the recipient gets the JWT, they can use the signature to verify the integrity of the token and trust the data inside.
JWT Vs. OAuth: Key difference
JWT vs. OAuth can seem similar at first, but they solve different problems in authentication and authorization, and it's important to understand where each one fits best.
| Feature | JWT | OAuth |
|---|---|---|
| Purpose | Token format | Authorization framework |
| Token Type | Self-contained token | Access tokens issued via flow |
| Use Cases | APIs and internal user authentication | Social logins and delegated access |
| User sessions storage | It is stateless because it has no server-side session needed. | It often uses tokens with expiration and refresh flows. |
| Dependency | No third-party required | Involves identity providers |
| Flexibility | Custom implementation | Standardized flows |
Can I Use OAuth and JWT Together?
Yes, and it’s quite common! OAuth issues tokens, which can be JWTs. In this case, OAuth handles the authorization flow, while JWT serves as the token format for carrying user information.
For example, when you log in with a service like Google (using OAuth), Google sends a JWT as your access token. Your app can then decode this token to verify the user's identity and determine what they're allowed to do.
Here’s a simple example of how OAuth and JWT work together in the Authorization code flow:
# Step 1: Redirect user to OAuth provider's authorization URL
import webbrowser
oauth_url = "https://accounts.google.com/o/oauth2/v2/auth"
client_id = "YOUR_CLIENT_ID"
redirect_uri = "http://localhost/callback"
scope = "openid profile email"
# Build the authorization URL
authorization_url = f"{oauth_url}?response_type=code&client_id={client_id}&redirect_uri={redirect_uri}&scope={scope}"
# Redirect the user to the OAuth provider's authorization page
webbrowser.open(authorization_url)
Once the user authorizes the app, they are redirected with an authorization code. The next step is to exchange this code for a JWT:
# Step 2: Exchange the authorization code for a JWT (access token)
import requests
authorization_code = "AUTHORIZATION_CODE_FROM_REDIRECT" # The code you get back after user authorization
token_url = "https://oauth2.googleapis.com/token"
client_id = "YOUR_CLIENT_ID"
client_secret = "YOUR_CLIENT_SECRET"
redirect_uri = "http://localhost/callback"
# Request to exchange the authorization code for an access token (JWT)
data = {
"code": authorization_code,
"client_id": client_id,
"client_secret": client_secret,
"redirect_uri": redirect_uri,
"grant_type": "authorization_code",
}
response = requests.post(token_url, data=data)
token_data = response.json()
jwt_access_token = token_data['access_token']
print(f"Access Token (JWT): {jwt_access_token}")
Finally, you can use the JWT to authenticate requests to a protected API:
# Step 3: Use the JWT to make authenticated requests
api_url = "https://www.googleapis.com/oauth2/v1/userinfo"
headers = {
"Authorization": f"Bearer {jwt_access_token}",
}
response = requests.get(api_url, headers=headers)
# Output the user info received from the API
print(response.json())
Conclusion
OAuth and JWT aren’t direct rivals, they solve different problems. JWT is a format; OAuth is a protocol. Use JWT when you need to authenticate users and manage sessions yourself. Use OAuth when you need third-party login or secure delegated access. Or better yet, use them together for a robust and secure solution.
Understanding the difference will help you build safer and smarter applications.
Frequently Asked Questions
What is the difference between a CSRF token and a JWT (JSON Web Token)?
CSRF tokens are used to protect against Cross-Site Request Forgery attacks by validating the origin of requests, while JWTs are authentication tokens often used for user identity verification.
How does Verpex ensure the security of my CRM data?
Verpex employs multiple layers of security measures to protect your CRM data. This includes using advanced firewalls, secure data centers, regular security updates, and SSL encryption for data transmission. Additionally, we conduct frequent backups to ensure data recovery in case of any security incidents.
How can organizations ensure security when implementing Microservices in web development?
Ensuring security in Microservices involves implementing robust authentication and authorization mechanisms, securing communication between services using encryption, regularly updating dependencies to patch security vulnerabilities, and conducting thorough security audits and testing.
Who is responsible for PHP bugs and security issues?
Any fixes will primarily be covered by the PHP developers, and regular updates are pushed out. Under a managed hosting solution, Verpex will make sure any updates are applied to your site as soon as they’re ready.

Joel Olawanle is a Software Engineer and Technical Writer with over three years of experience helping companies communicate their products effectively through technical articles.
View all posts by Joel Olawanle





















