Securing multiple domains with SSL can be expensive and complicated when each domain requires its IP address or certificate. Server Name Indication (SNI) and Multi-Domain SSL Certificates (SAN certificates) offer two practical solutions. SNI allows separate certificates on a single IP, while SAN certificates secure multiple domains under one certificate.
This guide explains how each option works, their differences, benefits, and limitations so you can choose the best SSL strategy for your hosting environment.
What is SNI (Server Name Indication)?
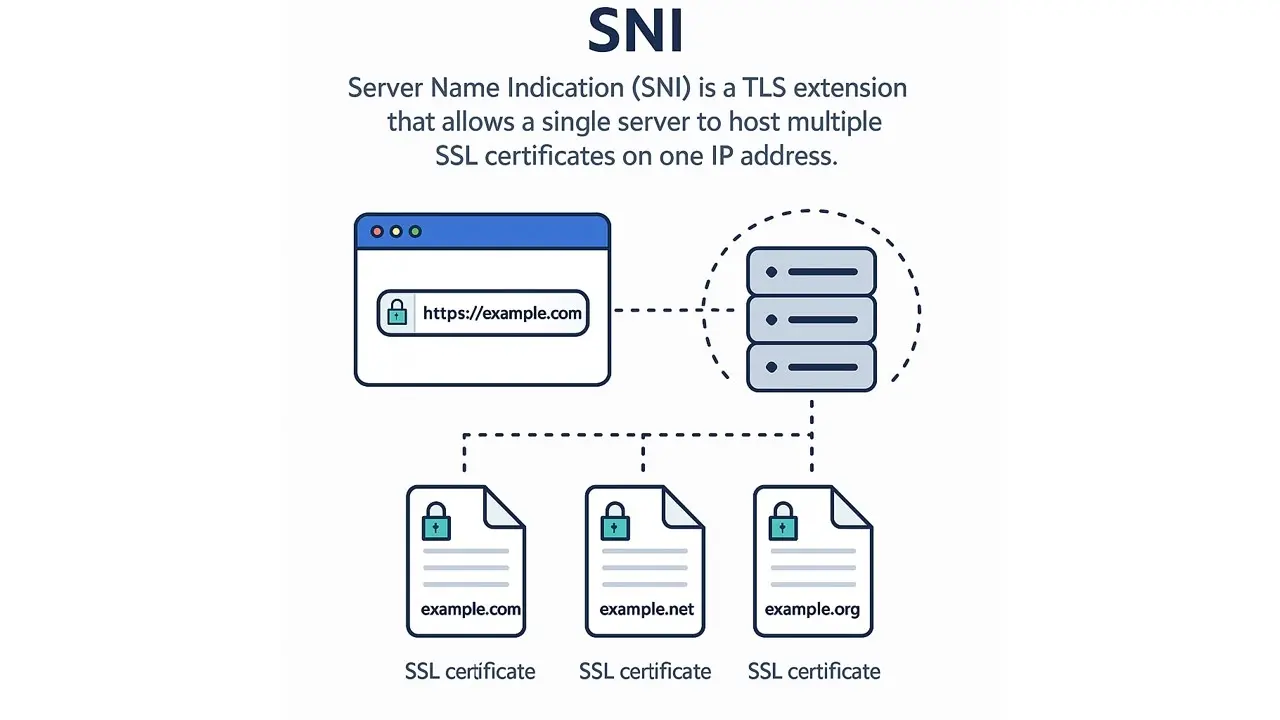
Server Name Indication (SNI) is a TLS extension that allows a single server to host multiple SSL certificates on one IP address.
When a browser connects via HTTPS, it includes the domain name during the TLS handshake.
The server uses this information to present the correct SSL certificate for that domain. This makes SNI ideal for shared hosting, VPS, and multi-site environments where assigning a unique IP to each domain is not practical.
Benefits and Limitations of SNI
Benefits
Limitations
Benefits of SNI
Eliminates the need for multiple IP addresses: Before SNI, securing multiple domains required dedicated IPs, which increased costs and resource allocation.
Cost-effective for shared hosting: Web hosting providers can serve multiple domains securely on a single IP, reducing infrastructure expenses.
Scalability: Easily add new SSL certificates without changing server configurations or acquiring additional IP addresses.
Widespread support: Most modern browsers and operating systems support SNI, making it a reliable solution for today’s web.
Limitations of SNI
Compatibility issues with older systems: Legacy browsers, such as Internet Explorer on Windows XP, do not support SNI, potentially leading to SSL errors.
Server dependency: The hosting server must be configured to support SNI, which may not be available on some outdated platforms.
Overall, SNI is a practical and scalable SSL solution for hosting multiple secure domains without the hassle of managing multiple IP addresses. However, for businesses with legacy system dependencies, alternative solutions like Multi-Domain SSL certificates may be a better fit.
What is a Multi-Domain SSL Certificate?

A Multi-Domain SSL Certificate, also known as a SAN (Subject Alternative Name) certificate, secures multiple domains and subdomains under a single certificate by leveraging the SAN field.
This allows administrators to include several domain names, such as example.com, example.net, and shop.example.org, within one certificate, eliminating the need to manage separate SSLs for each domain. The result is a cost-effective, streamlined solution ideal for businesses with multiple online properties.
Benefits and Limitations of Multi-Domain SSL Certificates
Benefits
Limitations
Benefits of Multi-Domain SSL Certificates
Simplified management: One certificate covers multiple domains, reducing the effort needed for tracking, renewing, and installing individual SSLs. Ideal for businesses with several sites.
Cost-effective security: More affordable than managing separate certificates, especially for e-commerce platforms using multiple domain extensions.
Broad compatibility: It works seamlessly across all modern and legacy browsers, unlike SNI, which may fail on outdated systems.
Strong encryption and trust: Provides the same level of protection as single-domain SSLs, ensuring secure data transmission across all domains.
Scalable for resellers: This simplifies SSL deployment for hosting providers managing multiple client domains under one certificate.
Limitations of Multi-Domain SSL Certificates
Higher upfront cost: Multi-Domain SSL certificates typically cost more than single-domain or wildcard SSL certificates, as they cover multiple domains under one issuance.
Limited flexibility if domains change frequently: Adding or removing domains requires reissuing the certificate, which can be inconvenient for organizations with frequently changing domain structures.
Key Differences Between SNI and Multi-Domain SSL
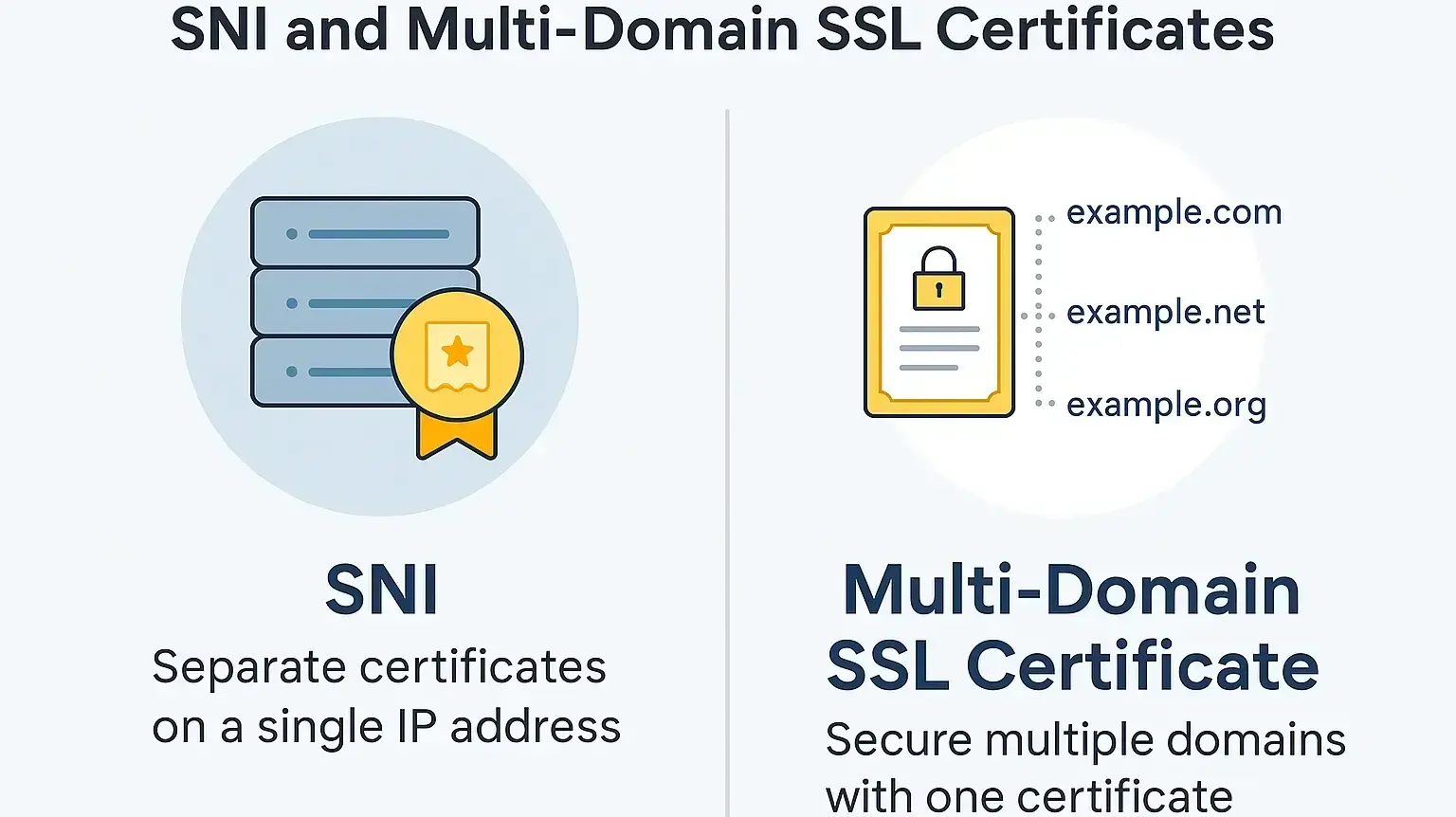
When deciding between Server Name Indication (SNI) and Multi-Domain SSL Certificates, it is essential to understand their differences in flexibility, cost, compatibility, and use cases.
| Feature | SNI (Server Name Indication) | Multi-Domain SSL Certificate (SAN) |
|---|---|---|
| How It Works | Hosts multiple SSL certificates on a single IP address by indicating the requested domain during the TLS handshake. | Secures multiple domains under one SSL certificate using the Subject Alternative Name (SAN) field. |
| IP Requirements | No need for dedicated IPs; multiple SSL certificates can be hosted on a shared IP. | Can work with a single IP, but not necessary if the server supports SNI. |
| Flexibility | Highly flexible: different SSL certificates can be added independently. | Limited flexibility: new domains require reissuing the certificate. |
| Cost Implications | Lower cost, as individual SSL certificates are purchased separately. | Higher upfront cost but may be more affordable in the long run for organizations managing multiple domains. |
| Best Use Cases | - Shared hosting environments. - VPS and cloud hosting with multiple SSL-protected domains. - Development and staging servers. | - Businesses managing multiple domains under the same ownership. - E-commerce platforms with multiple domain variations. - Enterprises with different brands under one umbrella. |
| SSL Management | Requires managing multiple SSL certificates, each with its own expiration and renewal cycle. | Simplifies management by securing all domains with a single certificate. |
| Browser Compatibility | Not supported by very old browsers (e.g., Internet Explorer on Windows XP). | Works with all modern and legacy browsers, making it ideal for enterprise applications. |
| Security Considerations | Each SSL certificate operates independently, ensuring proper isolation of domains. | All domains are tied to a single certificate, meaning a compromise or expiration affects all covered domains. |
| Limitations | - Requires proper server configuration. - Not supported by outdated systems. | - Adding or removing domains requires reissuing the certificate. - Expensive compared to individual certificates. |
When to Choose SNI vs. Multi-Domain SSL
Choosing between Server Name Indication (SNI) and a Multi-Domain SSL Certificate (SAN) depends on how you manage your domains and SSL requirements.
Use SNI If:
1. You are on shared hosting: You manage multiple domains on a shared server and need separate SSLs without requiring extra IP addresses.
2. You use VPS or cloud hosting: You run a VPS or cloud environment with multiple secure websites needing independent certificates.
3. You want flexibility: Each domain can have its own SSL certificate, making it easier to update or change certificates individually.
4. You are cost-conscious: You need a budget-friendly way to secure multiple domains without investing in a more expensive Multi-Domain SSL certificate.
5. Your users are on modern browsers: Your audience primarily uses up-to-date browsers, as older systems like Internet Explorer on Windows XP do not support SNI.
Some outdated browsers and operating systems do not support SNI, which may trigger security warnings for those users.
Use a Multi-Domain SSL Certificate If:
1. You manage multiple domains centrally: You own and control several websites and prefer to secure all domains under a single certificate for easier management.
2. You are running an e-commerce or enterprise setup: You operate across multiple domains, such as example.com, example.net, and shop.example.com.
3. You need broad device compatibility: You want SSL encryption to work across all browsers and platforms, including legacy systems.
4. You prefer simplified renewals: You want to track and renew one certificate instead of managing multiple expiration dates.
If your environment involves frequent domain changes, relying solely on a Multi-Domain SSL Certificate can be limiting, as each update typically requires reissuing the entire certificate, often with added cost and effort.
In such cases, a hybrid approach offers a more flexible and efficient solution using SNI for dynamic setups like reseller hosting or VPS environments where individual SSL management is needed and Multi-Domain SSL for stable corporate websites where domains remain consistent, simplifying administration and reducing overhead.
By aligning your SSL strategy with your hosting environment and operational needs, you can achieve the right balance of security, cost-efficiency, and long-term manageability.
How to Set Up SNI-Based SSL Certificates & Multi-Domain SSL Certificates
Securing multiple domains with SNI (Server Name Indication) or a Multi-Domain SSL Certificate (SAN SSL) requires different setup approaches. Below are step-by-step guides for both options.
Setting Up SNI-Based SSL Certificates on a Server
Step 1: Check SNI Support on Your Server
Before configuring SNI, ensure your server and web server software (Apache, Nginx, or IIS) support it. Most modern servers do, but older systems might require an update.
- Check Apache version:
apachectl -v
- Check Nginx version:
nginx -V | grep --color=auto "TLS"
- Check IIS version: IIS 8.0 and newer support SNI natively.
Step 2: Obtain SSL Certificates for Each Domain
For SNI, each domain requires its own SSL certificate. You can generate a Certificate Signing Request (CSR) and obtain SSL certificates from a trusted Certificate Authority (CA).
- Generate a CSR for each domain (Linux-based servers):
openssl req -new -newkey rsa:2048 -nodes -keyout example.com.key -out example.com.csr -subj "/CN=example.com"
- Submit the
.csrfile to your chosen CA to get an SSL certificate.
Step 3: Configure SNI on Your Web Server
1. Apache Configuration
Open your Apache configuration file (usually /etc/apache2/sites-available/default-ssl.conf).
- Define separate VirtualHost blocks for each domain
<VirtualHost *:443>
ServerName example.com
SSLEngine on
SSLCertificateFile /etc/ssl/example.com.crt
SSLCertificateKeyFile /etc/ssl/example.com.key
</VirtualHost>
<VirtualHost *:443>
ServerName example.org
SSLEngine on
SSLCertificateFile /etc/ssl/example.org.crt
SSLCertificateKeyFile /etc/ssl/example.org.key
</VirtualHost>
- Enable SSL and restart Apache
a2enmod ssl
systemctl restart apache2
2. Nginx Configuration
Open your Nginx SSL configuration file (e.g.,
/etc/nginx/sites-available/default).Configure separate server blocks
server {
listen 443 ssl;
server_name example.com;
ssl_certificate /etc/nginx/ssl/example.com.crt;
ssl_certificate_key /etc/nginx/ssl/example.com.key;
}
server {
listen 443 ssl;
server_name example.org;
ssl_certificate /etc/nginx/ssl/example.org.crt;
ssl_certificate_key /etc/nginx/ssl/example.org.key;
}
- Restart Nginx
systemctl restart nginx
3. Windows Server (IIS) Configuration
- Open IIS Manager → Select the site → Click Bindings.
- Click Add → Choose HTTPS → Select the SSL certificate for the domain.
- Check "Require Server Name Indication (SNI)".
- Repeat for other domains → Click OK → Restart IIS.
Step 4: Verify SSL & SNI Implementation
Use an SSL checker tool (e.g., SSL Labs' SSL Test) to verify that SNI is correctly set up. Ensure that modern browsers can access the site securely.
How to Obtain and Install a Multi-Domain SSL Certificate
Step 1: Choose a Certificate Authority (CA)
- Select a trusted Certificate Authority (CA) that offers Multi-Domain SSL (SAN) certificates, such as DigiCert, Sectigo (formerly Comodo), GlobalSign, or Let’s Encrypt (which provides limited SAN support).
Step 2: Generate a Certificate Signing Request (CSR) for Multiple Domains
- Use OpenSSL to generate a CSR including multiple domain names:
openssl req -new -newkey rsa:2048 -nodes -keyout mykey.key -out mycsr.csr -subj "/CN=example.com" -addext "subjectAltName=DNS:example.com,DNS:example.net,DNS:example.org"
Submit the CSR file to your CA when purchasing the Multi-Domain SSL certificate.
Once the CA issues the certificate, download the SSL certificate files.
Step 3: Install the Multi-Domain SSL Certificate
1. Apache Configuration
Open your Apache SSL configuration file.
Update the VirtualHost configuration to reference the SAN certificate:
<VirtualHost *:443>
ServerName example.com
ServerAlias example.net example.org
SSLEngine on
SSLCertificateFile /etc/ssl/multi-domain.crt
SSLCertificateKeyFile /etc/ssl/multi-domain.key
</VirtualHost>
- Restart Apache
systemctl restart apache2
2. Nginx Configuration
Open the Nginx configuration file.
Reference the SAN certificate in the server block
server {
listen 443 ssl;
server_name example.com example.net example.org;
ssl_certificate /etc/nginx/ssl/multi-domain.crt;
ssl_certificate_key /etc/nginx/ssl/multi-domain.key;
}
- Restart Nginx
systemctl restart nginx
3. Windows Server (IIS) Configuration
Open IIS Manager → Select the website → Click Bindings.
Click Add → Choose HTTPS → Select the Multi-Domain SSL certificate.
Click OK → Restart IIS.
Step 4: Add and Renew Domains in a SAN Certificate
Some CAs allow adding domains to a Multi-Domain SSL certificate during renewal.
If adding new domains, generate a new CSR and request a certificate reissue.
Limitations for SNI and Multi-Domain SSL Certificates
While SNI and Multi-Domain SSL Certificates (SAN Certificates) are efficient for securing multiple domains, each has limitations. Applying the right best practices helps maintain strong security and reliability.
1. Browser and Server Compatibility
SNI is not supported by some legacy systems like Internet Explorer on Windows XP, and older servers may need upgrades to handle it.
While Multi-Domain SSL Certificates work across all modern and legacy browsers, updating or removing domains requires reissuing the certificate, which can briefly disrupt service.
To avoid compatibility issues, test your SSL setup across various browsers using tools like SSL Labs’ SSL Test.
2. Expiration and Renewal Management
SNI requires tracking and renewing separate certificates for each domain, which can be time-consuming. With Multi-Domain SSL, a single expiration affects all linked domains, making timely renewal critical.
Use monitoring tools like Certbot, Let’s Encrypt auto-renew, or DigiCert CertCentral, and consider automating renewals with ACME clients to avoid lapses and reduce manual work.
3. Security Compliance
Using outdated protocols like TLS 1.0 poses risks, and in Multi-Domain SSL setups, a breach in one domain could impact others under the same certificate.
Enforce stronger encryption standards like TLS 1.2 or TLS 1.3, audit certificates regularly using tools like Qualys SSL Labs, and consider isolating high-risk domains with individual certificates for better protection.
Conclusion
Securing multiple domains efficiently requires choosing the right SSL strategy based on your hosting setup and long-term goals. SNI offers flexible, low-cost SSL deployment on a single IP, making it ideal for shared hosting, VPS, and dynamic environments.
Multi-Domain SSL Certificates, on the other hand, simplify management by securing several domains under one certificate, perfect for stable business portfolios and enterprise use Choose SNI if flexibility and per-domain control are your priorities, or opt for a Multi-Domain SSL Certificate for centralized management and universal compatibility.
Evaluate your hosting needs, explore options from trusted providers like DigiCert, GlobalSign, or Sectigo, and follow our setup guide to implement the SSL solution that fits your goals.
Frequently Asked Questions
Can a single IP address host multiple TLS certificates for different domains?
Yes. Using the Server Name Indication (SNI) extension of the TLS protocol, a single IP address can host multiple TLS certificates. During the handshaking process, the browser includes the hostname, allowing the server to present multiple certificates for different domains on one server. This enables efficient SSL setup for multiple websites or virtual domains without requiring a unique IP address per site.
What happens if a browser does not support SNI?
If a browser does not support SNI, the server cannot identify the requested hostname during the TLS handshaking process. As a result, it delivers a default certificate, which may not match the domain the user is trying to access leading to a browser warning or failed HTTPS connection. Most modern browsers support SNI, but some outdated ones do not, which can impact users trying to access secure connections on virtual hosts using SNI.
Can a single SSL certificate cover all the domains on one server?
Yes. A single SSL certificate, such as a Multi-Domain (SAN) certificate or Wildcard certificate, can cover all the domains hosted on one server, depending on configuration. While a Wildcard certificate secures subdomains under the same root (e.g., .example.com), an SAN certificate can protect multiple unrelated domains (e.g., example.com, example.net, example.org) with the same certificate.
How does SNI work with load balancers and other services?
When using a load balancer or other service in front of multiple sites, SNI ensures that the correct TLS certificate is used for each domain. The SNI extension passes the hostname during the TLS computer networking protocol negotiation, allowing the load balancer to route traffic correctly and establish a secure connection with the correct certificate even if the same IP address is used across sites.

Yetunde Salami is a seasoned technical writer with expertise in the hosting industry. With 8 years of experience in the field, she has a deep understanding of complex technical concepts and the ability to communicate them clearly and concisely to a wide range of audiences. At Verpex Hosting, she is responsible for writing blog posts, knowledgebase articles, and other resources that help customers understand and use the company's products and services. When she is not writing, Yetunde is an avid reader of romance novels and enjoys fine dining.
View all posts by Yetunde Salami




















