If you have ever saved a password to Google Password Manager, you've likely seen a pop-up warning that your password appeared in a data breach and should be changed.
Many applications include password strength checkers to guide users on creating strong password. Strong passwords are essential because they make it difficult for attackers to crack.
Apart from encouraging strong passwords, applications implement techniques such as hashing and salting to protect passwords stored in their systems. These methods are crucial in data security, authentication, and database management to safeguard sensitive user information.
This article will explain how they serve different roles in authenticating and protecting users' data from data breaches or attacks.
What is Hashing?
Hashing is a technique used to convert data, such as text, files, and numbers, into a fixed-length string of characters (called a hash value) using a mathematical function called a hash function.
Hashing is a one-way process, meaning that hashed data cannot be reversed to its original form. While hashing and encryption both transform data, they perform different tasks.
Hashing is irreversible and used for data integrity (strong passwords), while encryption is reversible, and encrypted data can be decrypted by the intended recipient to access the data.
The purpose of hashing includes:
- Strong password security
- File and data integrity
- Data security
- Threat detection
- Secure communication
Key Terms in Hashing
There are certain terms in Hashingthat you should know, including:
Input Data/Key
The input data hashed is called a Key. The key could be a string of text, an image, a file, or a number.
Hash Function
A hash function converts input data into a fixed-length string of characters regardless of the input data size. Some hashing algorithms or hash functions like those in SHA (Secure Hash Algorithm) operate with block sizes ranging from 160 to 512 bits.
For example, SHA-256 will generate a 256-bit hash value, which is represented as a 64-character string in hexadecimal format. If the input text is 100 characters long or a single value, the hash value would produce the same fixed-length output of 64 string characters.
Hash Value
A hash value is a number, or the output generated by a hash function, that provides a unique representation of the input data. It can be used for data authentication or digital signatures, or stored in a hash table for easy access or lookups.
Hash Tables
A hash table stores data, and it's one of the many ways to use hashing for data storage and retrieval.
For example, if you have a hash table with a lot of data, you can use the hash function to map a key to an index where a value is stored; it's much faster than arrays or linked lists.
Hashing Collision
In hashing, two different items may be assigned the same spot in a hash table or the same hash value, similar to people who share the same surname and first name called during an appointment. They would both respond at the same time.
When a collision occurs, the hash table finds a resolution. It can either chain two items to the same slot and in the slot, they are both stored in a list, or look for an open slot (called open addressing) to place the second item.
The many benefits of hashing include the following:
- Ensure data integrity
- Quick data retrieval
- Password storage
- Efficient caching
- Digital Signatures
- Data compression
- Database management
Types of Hashing Algorithms
Hashing algorithms are either cryptographic or non-cryptographic
Cryptographic and Non-cryptographic hash functions share similar properties that include:
Deterministic: For any given input, a hash function produces the same output. This means that as long as you use the same hashing algorithm, no matter how many times or where you run the function, the result will always be the same.
Non-reversible: A properly hashed value cannot be reversed to its original form.
Fast Computation: The Hashing algorithm should quickly process any data type into a unique hash value.
Collision Resistance: This makes sure that two different inputs do not produce the same hash.
The difference between these two hashing algorithms is that cryptographic hashes are designed to be secure and more suitable for tasks like:
- Data integrity
- Encryption
- Digital signature.
Here are a few popular cryptographic hashing algorithms, including:
- MD5(Message Digest 5)
- SHA (Secure Hash Algorithm)
- Blake2 and Blake3
Non-cryptographic hashing algorithms, on the other hand, are designed for speed and efficiency. These algorithms are used for indexing large data sets and for fast data lookup.
Non-cryptographic hashes are not designed for password security or digital signatures. Common use cases for non-cryptographic hashes include:
- Caching for fast data retrieval.
- Hash tables for storage and quick retrieval.
- Databases for indexing and partitioning.
- Checksums for data verification.
Here are a few examples of non-cryptographic hashing
- CRC32(Cyclic Redundancy Code)
- FNV (Fowler-Noll-Vo)
- MurmurHash
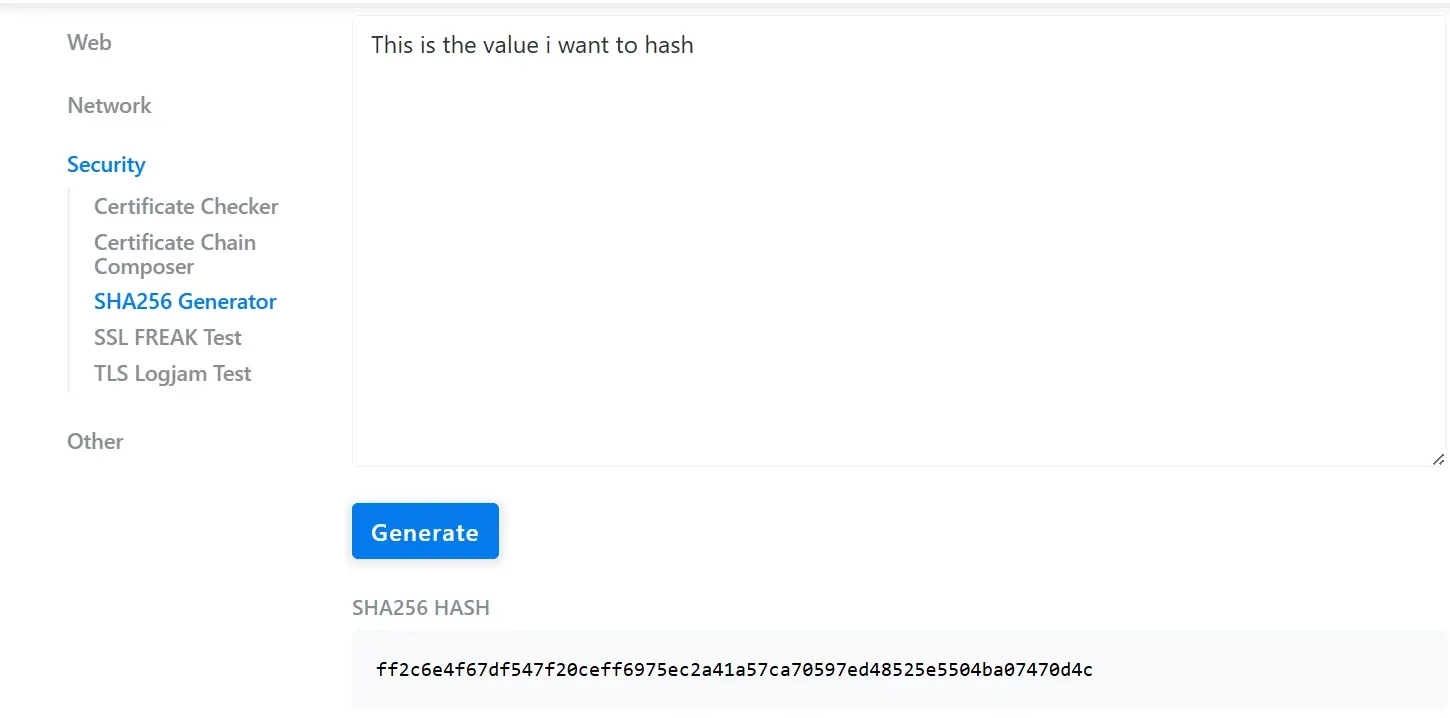
Let's see what hashing values look like using an online generator called KeyCDN. This online generator can help you generate a SHA256 hash of any string or input value instantly.
What is Salting?
>Salting is a technique for protecting passwords. It involves adding a random string of characters called a salt before hashing the password. This makes it hard for hackers to crack passwords using attacks like dictionary attacks.
How Salting Works
When a user submits a password through a form, the password receives a random piece of data called a salt before it is hashed.
Salting ensures that even if two users choose the same password, it adds a unique value to the passwords, resulting in different hash values.
Why is hashing alone not enough?
Hashing can be exploited through:
Rainbow Tables Attack
A rainbow table is a precomputed hash dictionary that contains a list of common passwords with corresponding hash values. If a hacker gets access to a database that stores hashed passwords (e.g., SHA-256 hashes), they can compare those hashes to each one in the rainbow table. If a match is found, they recover the original password.
Speed of Hash Functions and Brute Force Attacks
Some hash functions like MD5 and SHA-1 are fast, which is great for performance, but not for security.
Attackers can exploit this speed using powerful hardware like GPUs (Graphics Processing Units) to perform brute force attacks. GPUS can perform many calculations, enabling billions of password guesses per second. For example, a GPU like NVIDIA RTX 4090 can attempt up to 300 million password guesses per second.
In a brute-force attack, hackers guess billions of password combinations every second until a correct one is found. Typically, hackers guess many passwords, hash each guess, and compare it to the stored hash. If a match is found, they've cracked the password.
Importance of Salting
Salting improves the security of passwords as follows:
Prevents Hash Collision: Adding salt to a password prevents hash collision, which means, if two users have the same password, their hashes can be identical.
Salting makes passwords random, so if users have the same password, their hashes would be different, making it difficult for attackers to exploit common passwords.
Mitigate Dictionary Attacks and Brute-Force: In dictionary or brute-force attacks, attackers guess passwords and compare their hashes to stored hash values in a dictionary. Salting makes these attacks less effective due to the unique string in every password before hashing.
Increase Password Complexity: Salting a password adds complexity to hashing process without the need for users to create more complex passwords.
Salting Limitations
Some limitations of salting include:
Fast Hashing Function: A salted password can still be exploited if the hash function is too fast. To solve this, it is advised to use slower hash functions like bcrypt or Argon 2 that take more time and computer power to run, so that an attacker wouldn't be able to perform a brute force attack.
Limited Protection against all Attacks: Salting doesn't protect users from phishing or social engineering attacks where individuals are manipulated into sharing confidential information, or keylogging malware that captures keystrokes to steal passwords.
Salting doesn't prevent Weak Password: Creating a strong and unique password is also up to the user, even with salting, if a password is weak, it is vulnerable to brute force attacks, and the like.
The use of unique and very strong password is encouraged and many organizations enforce policies that require users to use complex passwords to prevent against exploitation.
Here’s a simple example of how salt can be used:
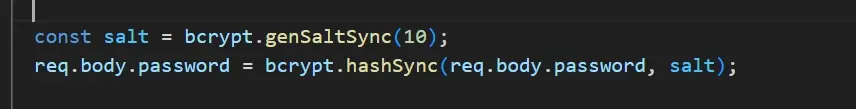
In the image above, the code is performing a password hashing with salt using bcrypt library.
const salt = bcrypt.genSaltSync(10): Generates a salt, and the salt is added to the password to make each password hash unique.
req.body.password = bcrypt.hashSync(req.body.password, salt): Hashes the password using the generated salt and replaces the plain text password in req.body with the hashed password.
Best Practices of Salting
Some best practices of salting passwords:
- Choose a secure hashing algorithm that is resistant to brute-force or dictionary attacks. e.g., bcrypt,
Ensure salt and hashed passwords are stored in a secure database to prevent unauthorised access.
Create a strong and unique salt for each password by using a Cryptographically Secure Pseudo-Random Number (CSPRNG) to produce unpredictable and secure salts.
Salt length matters because it determines the number of possible unique salt values. Short salts, like a 1-byte salt, are easily figured out, but longer salts ranging from 16 - 62 bytes, as encouraged by security experts, are more resistant to attacks.
Hashing vs. Salting
| Hashing | Salting |
|---|---|
| Hashing converts data into a fixed-length string. | Salt adds a random value to data before hashing. |
| Ensures data integrity. | Enhances security, ensuring passwords produce different hashes. |
| One-way process that cannot be reversed. | One-way process stored within a hash for data verification. |
| The same data produces the same hash. | Salt introduces a random value, ensuring that identical data has unique hashes. |
| Used for verifying data integrity and password storage. | Paired with hashing to secure passwords. |
Summary
Hashing transforms data into a fixed-length string, while salting adds an extra layer of security by introducing a random, unique value to produce different hashes. They both work in collaboration to secure passwords, protecting against dictionary, rainbow table, and brute force methods of attack.
Frequently Asked Questions
Can biometric security replace traditional passwords?
Biometric security can enhance or replace traditional passwords, offering a more secure and user-friendly authentication method. However, a combination of biometrics and passwords (multi-factor authentication) is often recommended for enhanced security.
How does Billing Software Hosting ensure data security?
Billing Software Hosting protects sensitive financial data with free SSL certificates and automated daily backups, ensuring secure connections and reliable recovery of important records. Additional security protocols are implemented to guard against unauthorized access.
How can I ensure data security with chatbots?
To protect customer data, implement encryption, access control, and regularly update your chatbot's security measures. Comply with data protection regulations and provide transparent privacy policies.
How does cryptographic erasure ensure data security, and what does it rely on?
Cryptographic erasure ensures data security by encrypting all the data on a data storage device and then securely deleting the encryption key. This makes the data encrypted and unreadable without the key. Cryptographic erasure relies heavily on strong encryption software and effective key management to achieve data sanitization and prevent unauthorized access.

Jessica Agorye is a developer based in Lagos, Nigeria. A witty creative with a love for life, she is dedicated to sharing insights and inspiring others through her writing. With over 5 years of writing experience, she believes that content is king.
View all posts by Jessica Agorye




















