Given the current state of the world, it is normal for individuals to make transactions online or use services that require inputting personal information or credentials. Similarly, organizations offer services that integrate through APIs, which may involve exchanging sensitive data.
To protect sensitive information, various techniques such as encryption, and hashing are employed.
Let us explore and compare encryption and hashing to understand how they are distinct and ensure data integrity, confidentiality, and security.
Encryption
Encryption is a security method that protects data by scrambling it using mathematical models so that only parties with the correct key can unscramble and access the data.
In simple terms, encryption means converting readable data into code, and it ensures the following:
- Confidentiality: Encryption ensures that data is kept private and is only accessible and understandable by authorized persons.
- Authentication: Authentication or authenticated encryption ensures data confidentiality, also known as privacy. Authentication verifies the origin of data, and confirms that it is from a trusted source.
- Integrity: Encryption alongside digital signatures ensures that data has not been altered since it was encrypted or corrupted intentionally or unintentionally in storage or transmission.
- Non-Repudiation: In cybersecurity, non-repudiation ensures that a party involved in a transaction cannot deny the authenticity of their digital signature. In other words, they cannot deny having sent or received a message or information. This helps verify the origin of data and ensures its integrity remains intact.
How Encryption Works in a Nutshell;
Encryption uses a set of mathematical values known as a cryptographic key or algorithm to convert readable data (plain text) into a random and unintelligible format called ciphertext.
To understand the encrypted message, the receiver uses a key to decrypt the ciphertext, converting it back into readable text.
The strength of encryption depends on the complexity of the key, which is classified based on the number of binary digits or bits it contains.
Commonly used algorithms include;
- 256-bit encryption for highly sensitive data that prioritizes security over speed.
- 128-bit encryption for user-friendly encryption or encryption where faster processing and usability are prioritized.
Older encryption methods such as 64-bit algorithms are becoming less secure as cybercriminals develop advanced techniques to decrypt them.
To understand why encryption is crucial for security, check out this article using this link.
Different types of encryption techniques used can depend on;
- Data being stored: This means data that is not actively moving, e.g. data stored in a cloud server or database.
- Data being transmitted: This means data being sent or received across networks or systems, e.g., logging into a website.
The main types of encryption, namely Symmetric and Asymmetric encryption, can be used in both cases, however, they are applied differently depending on certain requirements like speed, and security.
There are different types of encryption algorithms, such as:
- AES (Advanced Encryption Standard)
- RSA (Rivest-Shamir-Adlemen)
- CC (Elliptic Curve Cryptography)
- PGP (Pretty Good Privacy)
However, we will discuss only the two typesof encryption;
- Symmetric Encryption: This is a type of cryptography that uses the same key to encrypt and decrypt a message. This means that the key the sender uses to hide a message is the same key the recipient uses to reveal it.
The disadvantage of symmetric encryption is that it can be less secure, and data can be compromised when it gets into the wrong hands, so the key must be shared with authorized users only.
- Asymmetric Encryption:Asymmetric encryption is a type of cryptography that uses a pair of keys - a public and a private key to encrypt and decrypt data. Asymmetric encryption is more complex and secure for data transmission compared to symmetric encryption.
Because the keys are different, it would be difficult for a party who doesn't have the private key to decrypt it, even if they have access to the public key.
The Implications of not Using Encryption
Some implications of not using encryption include:
Data breaches: Encryption ensures that sensitive information like credit card information, passwords, and personal details are secure. Without encryption, this information would be susceptible to unauthorised access or data leaks, which can cause loss, reputation damage amongst others.
Weak Authentication: Authentication systems rely on users' credentials; without encryption, cybercriminals can steal usernames and other important details and use them to impersonate legitimate users for the sake of theft or vendetta.
Exposed Communication: Encryption secures communication between two or more parties. Collaborative platforms like emails or file-sharing systems are secure from eavesdropping, which can compromise the privacy and security of data or information.
What does a simple encryption method look like?
Let’s walk through a basic example of how data encryption works.
We will use the built-in crypto module. This Module provides cryptographic functionality that allows you to encrypt and decrypt data.
Note: The following code was written using the VS Code editor.
Step 1:
In the VScode terminal, type the following command: npm init -y
This is the command to set up a package.json file for your node.js project. It allows you to install packages like express, and crypto-js.
Note: If you haven't installed Node.js, you can visit the official website to download and install it.
Step 2:
Create two files in your project folder: index.js and server.js
index.js file: The index.js file starts up the express server.
server.js file: This server.js file contains sets up and configures the express app including route, and crypto setup.
Step 3:
Import the following required packages:
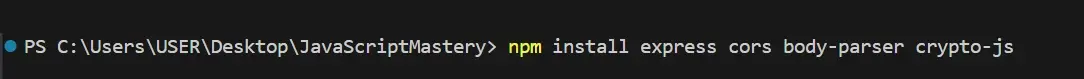
Express: A Node.js framework used to build APIs and web applications.
cors: Middleware that allows API calls from different domains.
body-parser: Parsed incoming request bodies in middleware.
crypto-js: JavaScript library for encrypting and decrypting data.
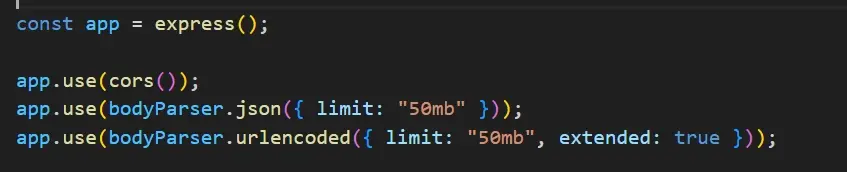
Step 4:
Set up the Express App and middleware
Step 5:
Create a GET request to the homepage where the user receives a message after visiting the URL.
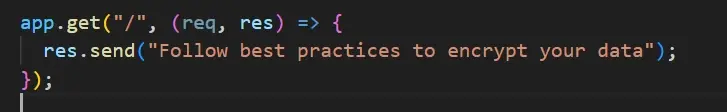
Step 5:
Create a GET request to the homepage where the user receives a message after visiting the URL.
Step 6:
Export the app object, which is the express app created in the server.js file.
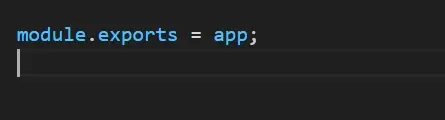
And, use it in the index.js file like so;
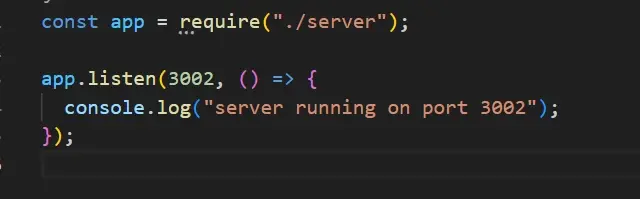
The above code means that you are importing the Express app (app) from server.js, and then you're telling the app to listen on port 3002.
This approach separates the server logic (server.js) from the code that starts the server (index.js).
Step 7:
Install nodemon to automatically start your server so you don't have to stop and re-start every time you make changes. In the JSON file, locate the script and do the following;
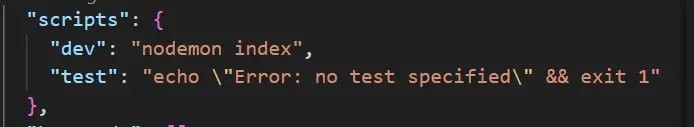
In your terminal, type the following command: npm run dev
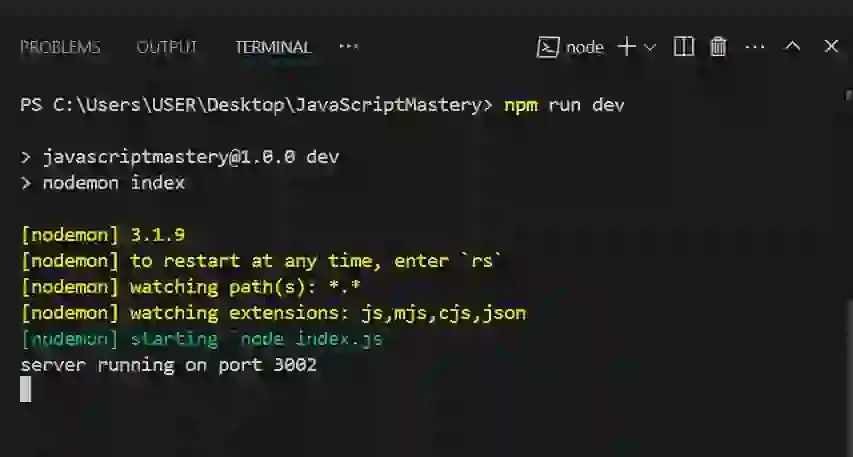
In your browser, type http://localhost:3002/. You’ll see the text sent from res.send In the get request handler within the "/" root route.
res.send is a response method to respond to the client running on localhost 3002. .
Step 8:
Create an encrypt Function
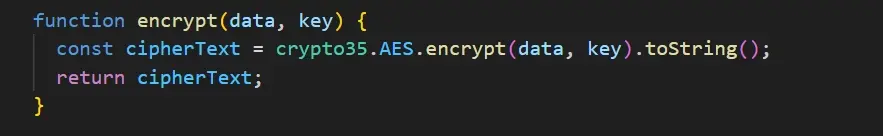
The function uses A9ES encryption from crypto-js to encrypt data using a key, and returns a ciphertext (encrypted string)
Step 9
Create a route to encrypt data
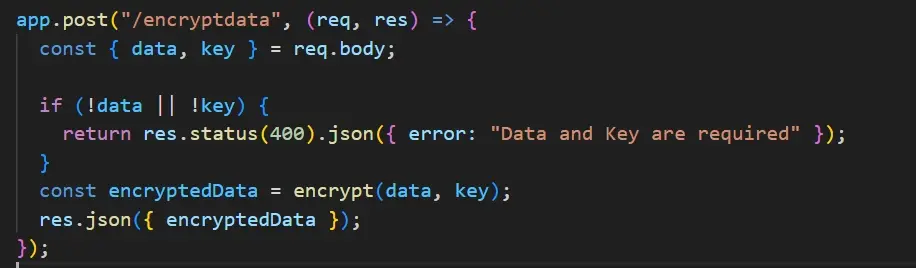
This route would receive a post request with data, and it would encrypt the data using a key.
Here’s a breakdown of what this code means;
This code handles a POST request to /encryptdata route, where it extracts data from the request body. It does the following:
Check if the data and key are provided.
Calls the encrypt function, which uses crypto-js to perform AES encryption to - - encrypt data using the provided key.
Sends the encrypted data as a response.
The encryptedData is the result of the encryption process. You will see this when you run the test.
Step 10: Test the API using Thunder Client.
Thunder client is an extension in VScode for testing APIs locally, you can use this instead of Postman.
In Thunder, the client tests the /encryptdata route by doing the following:
Enter http://localhost:3002/encryptdata in the URL bar.
- Select JSON format in the body section in Thunder Client and paste the following: { "data": "Follow best practices to encrypt your data", "key": "secretKey" }
Send the request by clicking the "Send" button
If everything is done correctly, you should get a response like the one in the image below.
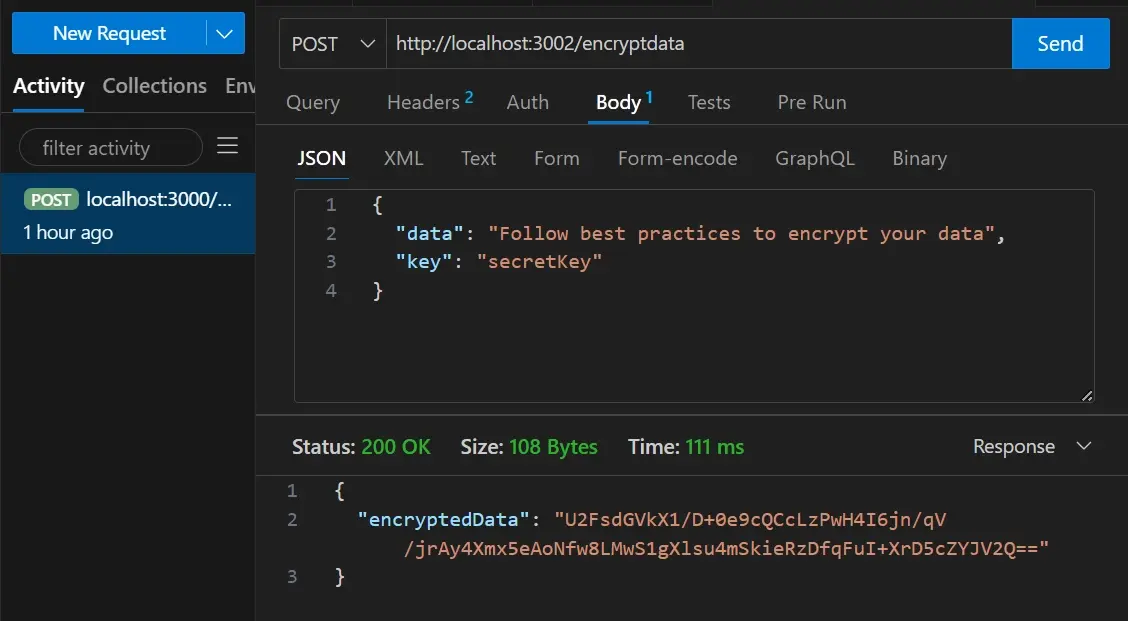
You can also create a function to decrypt this data, which will be discussed in another article.
Hashing
Hashing is a one-way mathematical function that turns data into a fixed-sized value called a hash for various purposes like ensuring data hasn't been tampered with and is secure.
Data hashed using a hashing algorithm becomes unreadable to humans and difficult to decrypt.
Here’s a basic example of how hashing works.
If you’re working with data storage in the backend of a website and you have a form that asks users for username and password, the form value is stored in a database like SQLite.
When saving the password, you wouldn’t want to save it in plain text, you have to securely hash a user's password before storing or processing it to make sure that even if the database is exposed users passwords remain secure.
To hash the password, you can use bcrypt, which is a package available in the Node Package Manager.
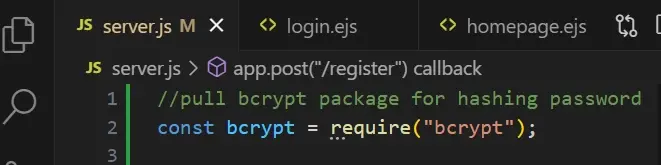
Then, in the data processing logic, we hash the password before saving it to a database.
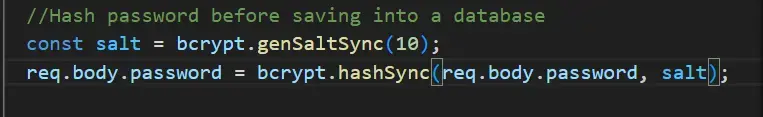
The code in the image above generates a salt, which is a random string that is added to a password before hashing. When the user enters their username and password, the hashed password will look like so;
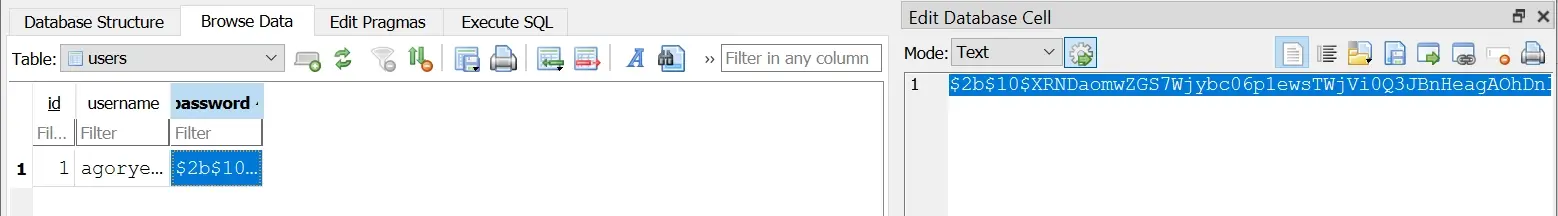
In the image, you can see how the password looks like a random string of characters.
Implications of not Using Hashing
Some implications of not using hashing include:
Exposed Passwords: If passwords are stored in plaintext, it's easy for attackers who gain access to a database to see sensitive information and exploit them.
Non-compliance with Industry Standards: There are strict compliance requirements for data security that many industries follow, like PCI-DSS for payment systems. If data isn't hashed it can lead to non-compliance which results in penalties.
Data Integrity Risks: Hashing isn't for storing passwords alone; it can be used to verify if data has been altered or modified during storage or transmission. Without hashing, files or data would be altered or destroyed without detection.
Use case Differentiating between Encryption and Hashing
Encryption: Encryption should be used when data needs to be secure with the intent of it being decrypted later, such as when you send a message that needs to be readable only by the intended recipient as it gets to its destination. A few use cases of encryption include:
- VPNS (Virtual Private Networks): Encryption is used to secure connections between your device and the VPN server protecting it from eavesdropping
Web Application: Encryption scrambles your password so that it is unreadable in case of a data breach.
Emails: Emails are often encrypted to protect them from being read by anyone other than the intended recipient.
Instant Messaging: Messaging platforms like WhatsApp use end-to-end encryption to ensure messages can only be read by the sender and recipient.
Online Payments: Encryption ensures that financial information like credit card details is transmitted securely over the internet during online transactions.
Hashing: Hashing is not reversible like encryption. This means that once data is hashed, you cannot get the original data back. Hashing is used in cases where data doesn't require decryption. A few use cases of Hashing include the following:
Password Storage: such as storing passwords in a database,
Data Integrity Verification: verifying the integrity of data to ensure it hasn't been altered.
Digital Signatures: Hashing serves as a digital signature or checksum. A checksum is like a digital fingerprint - it is a mathematical value assigned to a file to detect errors or any form of tampering during transmission.
Summary
In data security, encryption and hashing serve different purposes.
Encryption is used for data confidentiality, meaning that data is hidden until it gets to the recipient who has the authority to access it, while hashing is used for data integrity and verification meaning that it verifies the data, and is used to store sensitive data securely. Both are necessary depending on the context of usage.
Frequently Asked Questions
What is the difference between masking and encryption?
Masking focuses on hiding or disguising sensitive data without altering its format, while encryption transforms data into an unreadable format using cryptographic algorithms and keys to provide strong security and confidentiality. Masking is typically used for data presentation purposes, while encryption is employed to protect data from unauthorized access.
Can I use my encryption keys in cloud hosting?
Yes, many cloud hosts offer Bring Your Own Key (BYOK) services, allowing you to use your own encryption keys.
Check with your provider for setup details.
How does LiteSpeed handle SSL/TLS encryption and HTTP/3 in VPS environments?
LiteSpeed supports QUIC and HTTP/3 protocols, enhancing security and speed by reducing connection establishment times and encrypting traffic with modern SSL/TLS standards.
Can I use Port 465 for SSL-encrypted email transmission?
Yes, you can use Port 465 for SSL-encrypted email transmission. Port 465 was historically used for SMTP over SSL (SMTPS) and provides encryption using SSL (Secure Sockets Layer). However, Port 587 with STARTTLS is now the recommended choice for secure SMTP connections.

Jessica Agorye is a developer based in Lagos, Nigeria. A witty creative with a love for life, she is dedicated to sharing insights and inspiring others through her writing. With over 5 years of writing experience, she believes that content is king.
View all posts by Jessica Agorye





















