Role-Based Access Control (RBAC) is a security framework that regulates access to systems, data, and resources by assigning permissions based on user roles within an organization.
Rather than granting permissions directly to individuals, RBAC aligns access rights with predefined roles. These roles are designed to correspond to specific job functions, responsibilities, or organizational hierarchies, ensuring that users access only the resources necessary to perform their duties.
For example, a software engineer might have access to code repositories but not financial records, while an HR manager can view employee data but cannot modify critical IT infrastructure.
By defining roles and associating permissions to these roles, organizations can enforce a "least privilege" model, ensuring that users have only the access necessary to perform their duties.
For a better understanding, see the image created below:
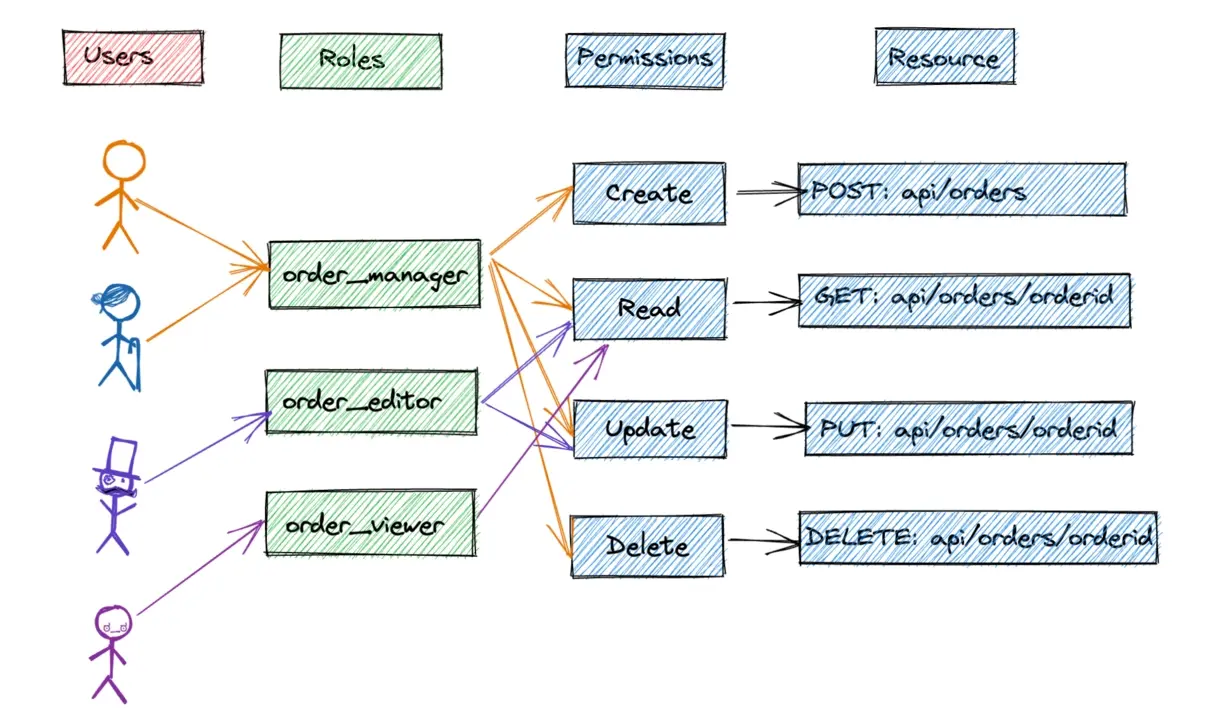
The image above shows different users with different levels of permissions, which helps to protect data from external threats and unauthorized access.
How RBAC Works
RBAC operates on a simple principle: people don’t get access to systems based on who they are, but rather on what role they have in an organization. Instead of giving individual employees specific permissions one by one, organizations group those permissions into roles and assign people to roles based on their job responsibilities.
This makes access control easier to manage, more secure, and scalable as the company grows. Let’s break down how it works into steps:
1. Define Roles Based on Job Functions
The first step in implementing RBAC is identifying the different roles within an organization and the access each one needs. A company might have roles like Employee, Manager, IT Support, Finance Officer, HR, or Administrator, each with different responsibilities. An Employee may only need access to basic company tools, while a Manager might require additional permissions to oversee their team’s performance or approve requests. Meanwhile, an IT Support specialist will need access to technical systems but shouldn’t be able to see financial data.
Defining these roles properly is crucial because it prevents unnecessary access. If roles are too broad, people might have more access than they need, creating security risks. On the other hand, if roles are too restrictive, employees may struggle to do their jobs efficiently. Finding the right balance is key.
2. Assign Permissions to Each Role
Once the roles are clearly defined, the next step is to determine what each role can and cannot do. Permissions are essentially rules that dictate what actions a user in that role can perform within a system. For example, an Employee might only have permission to view and edit their own files, while a Manager can access their team’s data and approve requests. An Administrator might have full control over user accounts and system settings.
This step ensures that access is structured logically. Instead of giving each user a long list of permissions manually, permissions are bundled into roles, making access control much more manageable. If someone moves to a different department, their access is adjusted by simply changing their role, rather than modifying multiple permissions one by one.
3. Assign Users to Roles
Once roles and their permissions are established, employees are assigned to the appropriate role based on their job. If Jane is a Manager, she is assigned the Manager role, automatically giving her the ability to review reports and approve employee requests. John, in IT Support, is placed in the IT Support role, granting him access to system logs but preventing him from viewing confidential employee records.
The beauty of RBAC is that if an employee gets promoted or switches departments, they don’t need to be given or removed from dozens of permissions manually. Instead, they’re simply reassigned to a new role that carries the appropriate level of access. This makes onboarding and offboarding employees significantly more efficient.
4. Enforce Access Based on Roles
Once roles and permissions are assigned, the system enforces them automatically. When a user logs in and tries to perform an action—whether it's opening a file, making a change, or accessing a report—the system checks their role. If their role includes permission for that action, they’re allowed to proceed. If not, access is denied.
For example, if a Finance Officer tries to access the company’s payroll system, they’ll be granted access because their role includes that permission. But if a Customer Support Agent tries to open the same system, the request will be blocked because payroll data is outside their job scope.
This enforcement happens in real-time and ensures that users only interact with the systems they are authorized to use. It also prevents security breaches by ensuring sensitive information is only accessible to the right people.
5. Use Role Hierarchies & Inheritance
In many cases, roles can have hierarchical structures, meaning higher-level roles inherit permissions from lower-level roles. This simplifies management and avoids redundancy. For example, a Manager may have all the permissions of an Employee, plus additional permissions to approve time-off requests and access performance reports. Similarly, an Administrator might have all the permissions of a Manager but also have control over system settings.
This approach ensures that roles are structured efficiently and reduces unnecessary duplication of permissions. Instead of assigning the same set of basic permissions to multiple roles, RBAC allows higher roles to inherit lower-level permissions, making access management more streamlined.
6. Apply Constraints & Security Rules
RBAC can also incorporate additional security rules to prevent misuse of access. One common practice is Separation of Duties (SoD), which ensures that no single person has too much control over a critical process. For example, in a financial system, the person who approves an expense should not be the same person who processes the payment. This prevents fraud and enhances accountability.
Other constraints can include time-based access, where employees can only access certain systems during work hours, or location-based access, where certain permissions are only granted when an employee is working from a secure company network. These extra layers of control help organizations further reduce security risks.
Key Components of RBAC
RBAC is built on a few fundamental components that define how access is structured and managed. These include Roles, Permissions, Users, Role Hierarchies, and Constraints. Each plays a crucial role in ensuring that access control remains efficient, scalable, and secure.
Roles: At the heart of RBAC are roles, which group users based on their job functions. Instead of assigning permissions directly to individuals, organizations assign permissions to roles, and then users are placed into roles. This simplifies access management, ensuring that people only get the access they need based on their responsibilities.
Permissions: Permissions determine what actions a role can perform. These are rules that grant or restrict access to files, applications, or databases. Instead of managing individual permissions for each user, RBAC assigns them at the role level.
Users: Users are individuals who are assigned to roles within the system. Each user belongs to at least one role, and through that role, they inherit the permissions necessary to perform their duties.
Role Hierarchies: Some roles inherit permissions from other roles, creating a hierarchy. This makes access control more manageable because it avoids unnecessary duplication of permissions. A higher-level role automatically includes all permissions of the lower-level roles beneath it.
Constraints (SoD & Other Rules): RBAC often includes additional rules to enhance security, such as SoD and other access restrictions. These constraints ensure that users cannot have conflicting permissions that might lead to security risks or fraud.
The Benefits of RBAC
Improved Security: RBAC reduces the attack surface by rigorously limiting access according to role permissions. It successfully reduces the risk of both external and insider threats by putting the principle of least privilege into practice, which limits users to the resources required for their jobs.
Simplified Management: The centralization of access permissions through roles significantly enhances administrative efficiency. Role assignments can be bulk managed, allowing for rapid adjustments during organizational changes, such as mass role assignments during onboarding or transitioning personnel through departments.
Regulatory Compliance: RBAC inherently supports compliance with regulatory frameworks such as HIPAA, GDPR, and SOX by controlling who has access to sensitive data. Its audit-friendly structure simplifies the demonstration of compliance through clear access logs and traceability of permission assignments and changes.
Efficient Onboarding and Offboarding Processes: The systematic assignment of roles allows organizations to accelerate the onboarding process, enabling immediate access to necessary resources for new hires. Conversely, as personnel exit or transitions occur, roles can be seamlessly adjusted or revoked, ensuring that access rights do not linger beyond employment without rigorous oversight.
Reduction of Operational Errors: The clear delineation of roles and associated permissions fosters a disciplined access approach that minimizes the potential for human error, such as unauthorized data manipulation or access. Role definitions serve as a safeguard against inadvertent security lapses.
Scalability and Flexibility: As organizations evolve, RBAC supports scalability by allowing the dynamic creation and modification of roles without significant infrastructural overhaul. This flexibility ensures robust access management capabilities as user populations grow or structural changes occur.
RBAC vs Other Access Control Models
Access control is essential for protecting sensitive data and systems, but RBAC isn’t the only approach and each has its strengths and weaknesses, depending on the security needs of an organization.
| Feature | RBAC (Role-Based) | DAC (Discretionary) | MAC (Mandatory) |
|---|---|---|---|
| Control Type | Centralized, based on roles | Decentralized, controlled by data owner | System-enforced, based on security labels |
| Who Sets Permissions? | Administrators assign roles and permissions | Individual users manage their own access | System enforces strict rules |
| Flexibility | Medium – Roles can be adjusted | High – Users can modify access easily | Low – Strict, predefined security levels |
| Security Level | High – Reduces human error | Low – Users may accidentally grant access | Very High – Enforced by strict policies |
| Use Case | Businesses, enterprises, cloud environments | Personal use, operating systems | Government, military, classified data |
| Risk of Over-Permissioning | Medium – Can be avoided with proper role design | High – Users may over-share access | Low – Strict rules prevent over-access |
| Ease of Management | Easy – Roles simplify permission assignment | Hard – Permissions must be managed manually | Very Hard – Requires system-wide enforcement |
Wrapping up!
RBAC is a powerful and efficient way to manage access control, ensuring that users only have the permissions they need based on their roles. It enhances security, simplifies administration, and reduces risks like unauthorized access or human error.
However, RBAC isn’t a one-time setup—it requires regular audits and careful role management to stay effective. When properly implemented, it strengthens security, streamlines IT operations, and helps organizations stay compliant.
Frequently Asked Questions
Can server overloading lead to security vulnerabilities?
Yes, server overloading can create security vulnerabilities by straining server resources, discouraging timely software updates, and reducing vigilance towards security practices. Maintaining a healthy server environment is essential for robust security.
How does backpressure management work in WebSockets?
Backpressure in WebSockets is managed by implementing flow control mechanisms. If a client or server is unable to handle the incoming data rate, it can signal backpressure to slow down the data transmission. This helps prevent overwhelming the system and ensures smoother operation under heavy loads.
Is big data in demand?
Yes, Big Data is in high demand across various industries, including e-commerce, healthcare, finance, and more. Organizations seek to harness the power of data for insights, decision-making, and gaining a competitive edge.
How does error-handling middleware contribute to application robustness?
Error-handling middleware significantly contributes to application robustness by providing a centralized mechanism to catch and process errors. This prevents unexpected failures from disrupting the entire application.

Joel Olawanle is a Software Engineer and Technical Writer with over three years of experience helping companies communicate their products effectively through technical articles.
View all posts by Joel Olawanle




















