Every day, people spend a considerable amount of time on the internet, whether they’re surfing the web for personal interest or using the internet to run their companies, or businesses, this makes it easy to be a target for malicious attacks. This article will help you identify when you’re under a DDoS attack and share some helpful methods to use in mitigating an attack from happening.
What is a DDoS Attack?
A Distributed Denial-of-Service (DDoS) attack is a malicious attempt to disrupt the traffic of a targeted server, service, or network by overpowering the target with a flood of internet traffic. An attacker can interfere with a target server or network by causing a lot of traffic or congestion and deplete the bandwidth and resources, which leads to a complete outage or abnormal behavior. A DDoS attacker uses other people's devices by spoofing and reflection, making the source of the attack difficult to find.
Multiple systems are combined to attack one system, and that is why it is called a Distributed Denial of Service.
To carry out a DDoS attack, the attacker will have control over online machines and IoT devices (Internet of Things) such as sensors, gadgets, etc. These machines and devices are infected with malware and turned into a Bot. This group of Bots are called a BOTNET and are used to carry out multiple attacks that give the attacker control over a network of hijacked computers and devices.
The objective of a DDoS attack is to avert the legitimate use of a website or application by causing chaos and defacement. It can also be a smokescreen to hide other illegal activities.
Three main types of DDoS Attacks

Volumetric Attacks: This type of attack is executed by using a bot to overload web links, application traffic, or connectivity with illicit requests, resulting in the rejection of regular and licit traffic. The target is overwhelmed with data packets to consume bandwidth and resources. It is also the most common type of attack, according to the 2022 Application Protection Report, 59% of DDoS attacks are Volumetric. It is easy to detect a Volumetric attack since it’s conspicuous, incoming traffic volts to bizarre levels like Gigabit or even Terabit over usual traffic making it easy to spot. The volumetric attack is quantified in Bits per second (Bps) and Gigabits per second (Gbps) flood.
Application Layer Attacks: These types of attacks are achieved by targeting the application, focusing on its weakness which in turn causes the application's inability to deliver content to the user. The attack influences web traffic by targeting the HTTP GET/POST floods, DNS, HTTPS, and SMTP protocols, replicating the usual online traffic. This makes it arduous to detect and fix, and It is measured in Requests per second (Rps) Flood.
Protocol Attacks: These types of attacks target network components used to validate connections by delivering Faulty and slow Pings to the network, targeting the firewalls and load balancers that consume the server's resources. The Layer 3 and Layer 4 protocol communications are flooded with malicious connection requests that crash or slow down the network or application making it impossible for anyone to use. It is measured in Packets per second (Pps) Flood.
In 2017, Google mitigated a 2.54 Terabyte Per Second (TBps) attack. Attackers targeted google services, and spoofed packets were sent to 180,000 web servers, which sequentially sent responses to Google. The attack lasted for 6 months and is recorded as the largest DDoS attack the company has ever faced to date.
Google didn’t disclose this attack until October 2020, they released the information to alert people on the increase of hacker groups abusing DDoS attacks with malicious intent. During this period of the attack, Google reported thousands of vulnerable servers to their network providers and also worked with network providers to trace the source of the spoofed packets so they could be filtered.
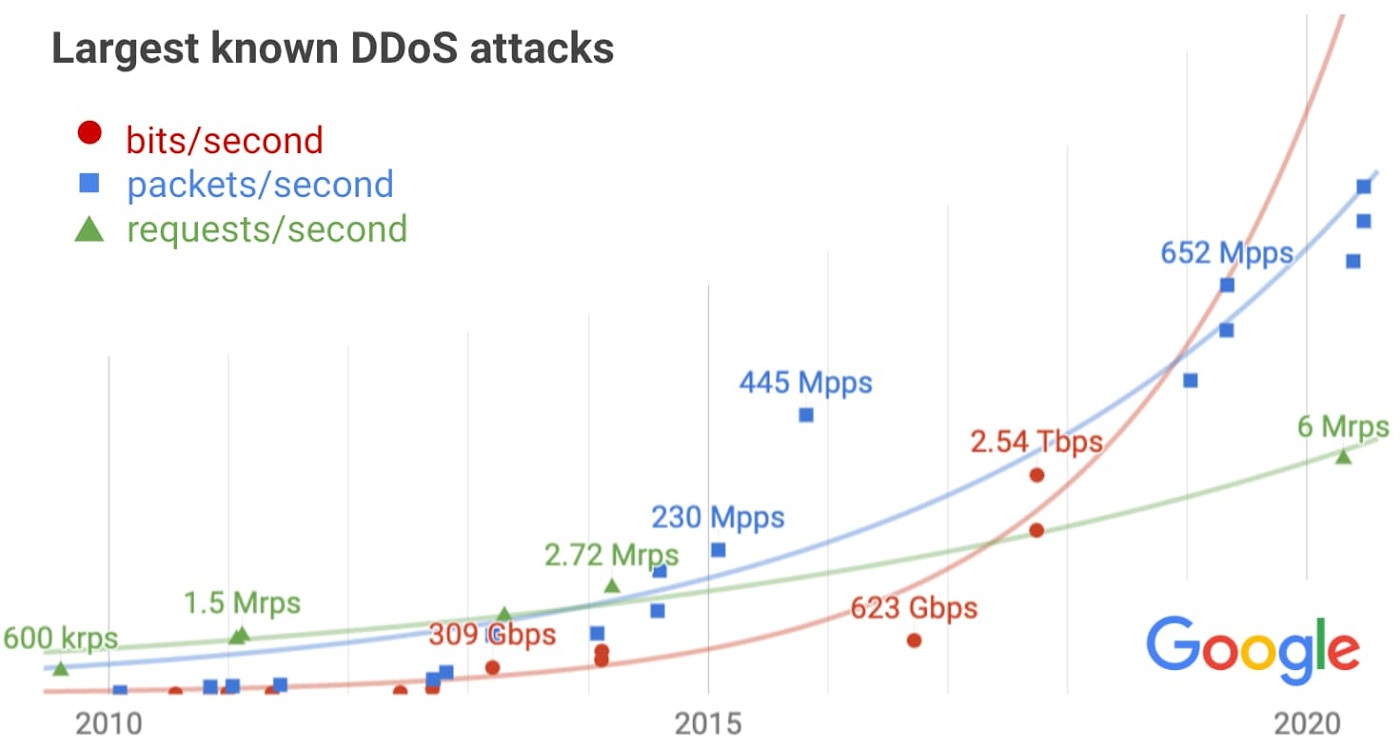
In 2021, the Microsoft Azure team prevented/mitigated an average of 1,1955 attacks per day in August, with the highest being 4,296, which occurred on August 10 . In the second half of 2021, there were 359,713 attacks in total.
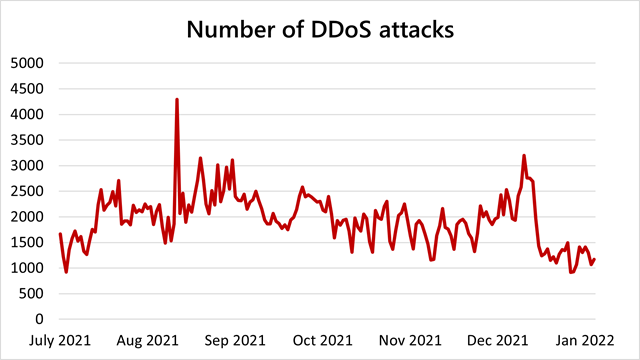
In May 2021, self-designated threat actor(s) ‘Fancy Lazarus’ began a crusade of distributed denial-of-service (DDoS) extortion attacks against several organizations.
The attack launched a demonstration DDoS attack on their target, then threatened to follow up with more disastrous attacks against essential assets unless the organization paid a fee via Bitcoin cryptocurrency.
A survey report from Cloudflare shows that in January 2022, over 17% of under-attacks were reported by respondents being targeted by ransom DDoS attackers. However that figure dropped drastically to 6% in February, and then to 3% in March.
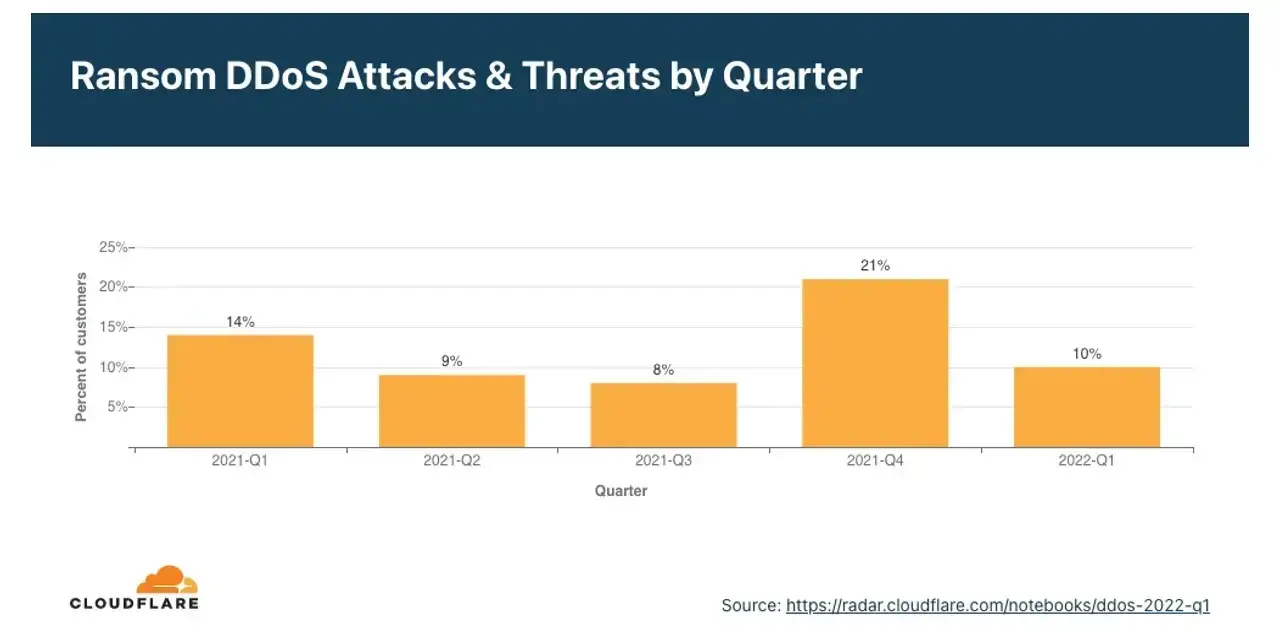
There was a drop in ransom DDoS attack in the first quarter of 2022 Q1 , with only 10% reported ransom DDoS attack; a 28% decrease Year-over-year (YoY) and 52% decrease Quarter-on-quarter (QoQ).
The top 10 sources of DDoS attacks are:
- China
- The U.S.
- Brazil
- India
- Malaysia
- Indonesia
- Russia
- Germany
- Ukraine
- Spain
Some commonly used DDoS attack types include
ICMP Flood: This attack is carried out by overwhelming the victim's computer with ICMP echo requests and echo reply also known as pings. When the network is flooded with these request packets, it causes a strain on incoming and outgoing channels of the network, consuming significant bandwidth which leads to a denial-of-service.
Slowloris: This type of attack allows an attacker to overwhelm a targeted server by utilizing partial HTTP requests. It uses a low amount of bandwidth and aims to use up server resources with requests that seem slower than normal but mimic the regular traffic.
HTTP Flood: This attack is done by overwhelming a targeted server with HTTP requests. The target is saturated with requests and is unable to respond to normal traffic which leads to denial of service.
UDP Flood: The User Datagram Protocol (UDP) is a communication protocol that is used across the internet for time-sensitive transmissions like Video Playback. This type of attack is done by sending packets to targeted servers with the intention of overwhelming the device's ability to process and respond.
Zero-day: Zero-day attack (also referred to as Day Zero) is an attack that takes advantage of a software security weakness that a developer or user is unaware of.
This attack can be prevented by updating operating systems, antivirus, and internet browsers automatically and by installing any recommended updates occasionally rather than waiting for the regular scheduled updates.
How to Identify you’re under a DDOS attack

Experience Slow Connections

Unresponsive Website
Your server responds with a 503 due to service outages

Internet connection issues
How to Prevent / Mitigate a DDOS Attack?

Create a Denial of service response plan: It is recommended that you go over your system to identify possible security flaws that may leave you open to malicious attacks and also align a clear response from your company in the case of a DDoS attack.
Secure your Infrastructure by DDoS Prevention Solutions: Security tools such as Firewalls, network monitoring software, threat monitoring system, Anti-Virus, and Anti-Malware can be used to monitor your base line traffic, you’re also able to set up alarms that will alert you when there’s some sort of unusual activity going on.
Take Note of warning signs: To detect a DDoS attack, here are a few warning signs to take note of. Network delay, excess spam, website shuts down all these signs indicate a DDoS attack, and you’re required to waste no time in taking the right action.
Cloud-Based Service Providers: Adopting cloud-based services can help reduce DDoS attacks, an example is Google Cloud Armor which detects and mitigate DDoS attacks automatically.
Monitor Unusual Activities: Monitor your traffic by looking out for abnormalities, including unexplained traffic spikes and visits from suspect IP addresses and geolocations. Attackers perform “dry runs” to test your defenses before carrying out more intense attacks.
Conclusion
You may wonder why these attacks happen? There are so many reasons attacks happen to name a few, financial gain, boredom, anger either from an employee or customer, cyber warfare, Ideology, Hacktivism, competition, desire for power, etc.
DDoS attacks consume resources and impact user experience in a negative way which causes service owners to invest more in resources like bandwidth or CPU memory, it can also cause havoc to a business's financial ability. As we advance more with the use of technology, houses, cars, and businesses that function with technology are likely to be prone to a DDoS attack.
DDoS attacks do not look like they’ll be disappearing soon in fact they may be on the increase. Individual users should ensure their computers and IoT devices are secured. There’s a need to take preventive measures to ensure that applications and infrastructure are completely guarded to avoid attacks that may be costly.
Frequently Asked Questions
What are the costs of a cyber-attack?
Besides losing a lot of money, cyberattacks also damage the reputation of a business. This is the reason why CEOs sometimes step down from their jobs after a cyber-attack.
What’s at risk with a cyber-attack?
If a cyber attacker accesses your network, they can do damage on several things, such as manufacturing processes, expansions plans, product designs, your pricing structure, your company’s banking details, customer credit card information, and access to client lists.
Will Verpex handle any VPS technical issues?
Yes, if you opt for a managed service Verpex will take care of all service and maintenance issues for you.
Why choose Verpex for WordPress?
As the leading CMS out there, we’ve made it our mission to offer the most comprehensive and streamlined WordPress solutions on the market. Backed by a responsive customer care team and reliable site enhancement tools, we ensure our users get the full WordPress value and support for a reasonable price.

Gift Egwuenu is a developer and content creator based in the Netherlands, She has worked in tech for over 4 years with experience in web development. Her work and focus are on helping people navigate the tech industry by sharing her work and experience in web development, career advice, and developer lifestyle videos.
View all posts by Gift Egwuenu


















